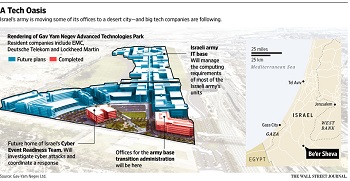
Why Is Snapchat More Secure than the Federal Government? by Andrea Castillo
Cyberhawks have seized upon this year’s massive hack of the Office of Personnel Management (OPM) to shove a wolfish surveillance bill in a sheepish cybersecurity bill’s clothing down America’s throat.
But the “Cybersecurity Information Sharing Act of 2015” (CISA) would have done nothing to stop the hack that exposed as many as 14 million federal employees’ personnel records. The pro-NSA crowd’s arguments are obvious nonsense — if anything, the OPM hack clearly demonstrates the danger of trusting incompetent government bureaucracies to manage huge datasets of sensitive personal information.
But amid all of the hubbub, these self-styled champions of strong cybersecurity — who also just happen to be anti-private encryption and pro-surveillance — have neglected to raise one important question: Why did a goofy picture-sharing app implement basic security measures before the central repository for all federal personnel data did?
This week, Snapchat announced that the private picture messaging service was offering two-factor authentication for its users. This basic measure of security helps to verify that the person logging in is indeed the legitimate owner of their account by sending out a text message with a special access code to the owner’s cell phone.
That way, a hacker must obtain both your password and your mobile phone to access and control your account. It’s simple, but simple security solutions can sometimes mean the difference between a foiled infiltration and a very, very bad day for a Snapchat user.
Of course, it is too much to expect the chief steward of federal employee information to implement such a simple policy. As the beleaguered office’s Inspector General reported last fall, OPM does not require multi-factor authentication to access its information systems.
If a careless OPM employee chose a weak and easy-to-guess password, or emailed it in plain text across an insecure channel, or merely left it on a sticky note on his or her desk (as is common practice in the federal government), than any common hacker could potentially access vast amounts of federal data.
In other words, an application for sharing pictures of wild parties and funny cats has better authentication standards than the federal government’s primary steward of millions of current and former federal employees’ and contractors’ addresses, Social Security numbers, financial information, and health records. Oh, and that of our military leadership and intelligence contacts — several of which are embedded deep undercover in dangerous missions — as well.
Hackers also accessed the feds’ cache of Standard Form 86 files for the aforementioned groups, dragging countless family members, friends, and colleagues into the databreach crossfire.
To call this a huge mess would be the second biggest understatement of the year. The biggest? That OPM’s substantial information security vulnerabilities are entirely unacceptable and directly at fault for the hack.
The OPM’s annual information security reports to Congress have admitted “material weaknesses” and “significant deficiencies” for years. The department lacked an IT team with “professional security experience and certifications”until 2013. Disgruntled employees could have merely walked off with this data if they wanted to, since OPM does not “maintain a comprehensive inventory of servers, databases, and network devices.” Nor did the OPM encrypt any of the data that the hackers stole — they might as well have just invited our forward friends in China to sweep in through the front door!
As Ars Technica’s Sean Gallagher concludes, “Considering the overall condition of OPM’s security, it’s no surprise that an attacker — almost any attacker — could gain a foothold inside the agency’s network. But attackers didn’t just gain a foothold, they had practically a free run of the networks.”
It’s true that Snapchat has hardly been a paragon of good cybersecurity in the past, as previous security vulnerabilities, breaches, misleading marketing, and the infamous “Snappening” testify. However, there is another important difference between Snapchat and the OPM that puts the humble app ahead of the mighty federal office: Snapchat has to learn from its mistakes.
As a private service provider in a hotly-competitive market that must keep its users happy to stay afloat, Snapchat moved quickly to get its security house in order after their big mistakes. They hired the former social network security leader for Google and started to build a “culture of security” within the firm.
They may still have a long way to go, but these investments and cultural prioritization are important first steps that demonstrate a proactive sense of ownership in their platform’s security. And of course, if they keep screwing up, they’ll be sued out the nose and go out of business for good.
We see no such sense of urgency with OPM. The agency received what could have been a saving wakeup call in last year, when it was discovered that Chinese hackers had accessed OPM databases in March of 2014.
OPM had the opportunity to implement simple encryption and authentication measures, tighten up their ship, and increase employee education about good data and security practices. No such luck! The office more or less continued on its merry way.
No one was fired back then and it looks like no one will get fired now. It’s government work, after all.
Unfortunately, OPM is hardly the only sucker on cybersecurity in the federal government, as my research for the Mercatus Center has found. This kind of unbelievably poor cybersecurity posture is the norm rather than the exception.
In fact, it’s hard to pick what is scarier: that the federal government operates under the digital equivalent of leaving all of their doors and windows unlocked and wide open, or that these same federal agencies want more power to manage your personal data through CISA.
Andrea Castillo is the program manager of the Technology Policy Program for the Mercatus Center at George Mason University and is pursuing a PhD in economics at George Mason University.