Have you heard of the shocking and terrifying diaper gap that is now dividing this nation? It is said to be so dire that the White House is urging immediate government assistance to buy baby diapers. Philosophically, this puts disposable plastic consumer products in the category of inalienable rights guaranteed by the government: among these are Life, Liberty, and the Pursuit of Diapers.
When I lived in the USSR, our Soviet Constitution also guaranteed that our basic needs be provided to us by the caring socialist government. As a result, most basic items were in shortage, let alone such luxury items as coffee or toilet paper. Needless to say, we never even heard of disposable diapers. For our three children, we used pieces of cloth which we washed regularly. We didn’t complain or feel disadvantaged because — I repeat — we had no idea there was such a thing as disposable diapers. Those only existed in the decadent West, where greedy corporations created such a product to boost their capitalist profits. But we were blocked from this information by the Iron Curtain, and what we didn’t know couldn’t hurt us.
Now I live in America, where the decadent capitalist diapers are about to become a basic “human right” guaranteed by the federal government.
About twenty years ago no one used cell phones because they hadn’t yet been created by greedy capitalist corporations, who have since covered the planet with a network of cellular towers. Now free cell phones — known as Obamaphones — have become a “human right” guaranteed by the government.
Internet service didn’t exist either, until greedy capitalist corporations surrounded the world with cables and satellites. Now Internet service has become a “human right” provided by the U.S. government to the needy.
Condoms, birth control pills, and other modern contraceptives also didn’t exist until they were invented, researched, and mass-produced by greedy capitalist corporations. Now they have become a basic “human right” guaranteed and provided by the government.
Vaccines for Ebola and other exotic diseases didn’t exist until they were developed by greedy capitalist corporations and almost immediately declared a “human right” for anyone in the Third World.
Healthcare with all its modern diagnostic equipment, appliances, treatments, and a vast array of pharmaceuticals, from Tylenol to Viagra, also didn’t exist until greedy capitalist corporations…
And so on and so forth.
Capitalism just keeps churning out all these new products, which our increasingly socialist government then declares “human rights” and taxes these very producers in order to provide their products to the people for free.
Some call it harmonious coexistence, but there’s a catch. The more the socialist government expands its functions by guaranteeing an ever expanding number of “human rights,” the more it needs to tax capitalist producers, which undercuts their ability to develop, manufacture, and market new products. Once they reach a tipping point when capitalism is no longer viable, this will also end the propagation of “human rights” in the form of new goods and services.
Socialism conserves the stage in which the society existed at the time it was overtaken. Cubans still drive American cars from the 1950s, North Koreans still dress in the fashions of the same bygone era, and in the USSR I grew up in a government-owned house that was taken from the rich and given to the needy in 1920s and remained without indoor plumbing or running water and with ancient electrical wiring until it was condemned and demolished in 1986.
A planned economy is mostly focused оn providing the basic needs that have already been declared “human rights,” and even then it struggles to keep up with the demand. The USSR had smart inventors and brilliant scientists, but the first personal computer was built in a Californian garage and not in a Siberian one — because America had free enterprise and the USSR didn’t. In the absence of free markets and competition, innovation becomes an almost insurmountable task. There is no time nor money for new products and services; that way it’s also easier for the government to run the economy. And when the people don’t know what they are missing, there’s no reason to be unhappy.
That, however, works best when the rest of the world no longer has competing capitalist economies and no nation lives better than the rest. For example, if it weren’t for capitalist America and Western Europe with their never ending innovation and higher living standards, it would have been a lot easier for Soviet citizens to remain content with their socialist government and thus the USSR would probably still exist.
But wouldn’t it be great if the entire world lived like one socialist village — even if it conserved some ancient technology — and people wouldn’t be missing any consumer products they knew nothing about anyway? Absolutely not — and for a reason that is allegedly dear to every socialist in the West: environmental protection. Centrally planned economies of the Eastern Bloc, China, and other socialist states inevitably became some of the world’s worst polluters.
On the one hand they were stuck with outdated technologies, and on the other they had no budgets for cleanup. Their grimy and polluting state-run factories had to meet their production quotas at any cost, for the glory of the Motherland — even if it meant the destruction of the Motherland’s environment and endangering the health of workers and local residents. Complaining to the state about the actions of the state would be pointless and often more dangerous than breathing bad air and drinking polluted water.
Having the entire world adhering to this model would have resulted in an environmental apocalypse and there would be no Greenpeace to bemoan it because that would mean economic sabotage and the activists would by default become enemies of the state.
Whatever innovations the Soviet planned economy introduced came from the West. The Soviet planners also learned from the West about the real cost of things in the modern world, since their own pricing mechanisms had been removed decades ago with the elimination of free markets.
Thus, socialists are better off with capitalism to invent new products that will be later declared “human rights,” allowing expansion of government functions to new areas, as well as to generate wealth that pays for socialist programs. Likewise, socialists are better off having the rich to subsidize the creation and mass production of new goods and services, and later to pay taxes so that the government can provide these goods and services to others for free.
This leads us to the following conclusions, which socialists can’t refute because it correlates with their own logic:
- The longer socialists wait to take over the power, the more technologically advanced society they will get to conserve.
- It is more beneficial for the people of all classes, including socialists, to delay the socialist revolution indefinitely.
- To delay the socialist takeover is also better for the environment because only capitalism has the power of innovation and the resources to create less polluting technologies, materials, and alternative energy sources. To impose socialism right away would mean to put the planet at risk of never resolving the environmental problems we face today.
- Since capitalism generates goods and services that socialists later designate as “human rights,” it is also in the interest of human rights to keep capitalism around indefinitely.
Socialists often describe the world as if it has always been as it exists today, leaving out the dimension of time. But time is a major factor because the world has never been static — and that includes nations, cultures, ethnicities, technologies, sciences, and popular perceptions, such as human rights. The main question that needs to be answered, therefore, is not as much who, where, and how — but “when?”
For example, switching to socialism directly from feudalism would have conserved the society at an early stage, without the host of various “human rights” that were unheard of at the time. According to Marx, humanity needed to go through the stage of capitalism in order to develop the necessary wealth, technologies, and educated populations before the socialists could take over.
But how do we know when the time is right for such a takeover? According to Marx and Lenin, a revolutionary situation exists when the upper classes no longer can, and the lower classes no longer want, to preserve the system, plus there exists a strong revolutionary party that can organize the masses.
Such a party, or rather a conglomerate of radical leftist movements, already exists — and it has been flexing its muscles in Ferguson, Baltimore, and most recently in Chicago, disrupting capitalist Donald Trump’s voter rally. But the first two preconditions for a socialist revolution in America simply do not exist because this country has never had natural static classes, such as the capitalist oppressors ruling over the oppressed workers and peasants. American society has always been dynamic, with unprecedented rates of upward mobility.
Socialists have been trying to update the Marxist formula by redefining “capitalist oppressors” as “hetero-normative patriarchy” and “oppressed workers and peasants” as “sexual, racial, ethnic, linguistic, and religious minorities,” but all their efforts to artificially polarize and destabilize the system have failed to create a revolutionary situation, despite all the tangible damage they have done to the country and to the minds of the growing generation.
Showing the lack of delayed gratification, socialists chant, “When do we want it? Now!” But if they had taken over, for instance, in the 1960s, Americans would have never been able to enjoy such “human rights” as free Internet, free cell phones, or free disposable diapers. Americans would be living today the way we lived in the USSR around the 1980s. There would be no affordable personal computers, tablets, eBooks, iTunes, Google, YouTube, Facebook, or Twitter.
Now that all these capitalist wonders exist, is it finally time? What if we miss the next life-changing technological development that will happen in a year or two? What if it will be a new cheap and clean energy source that will make fossil fuels obsolete? What if it will become a new “human right” that will make all the previous “human rights” pale in comparison?
Speaking of which, how do we know when is a good time to declare the next consumer product a “human right”? If we are serious about it, there has to be a mathematical formula that allows us to calculate with precision the exact time when any given product is no longer a novelty but a “human right.”
This is how the process happens today, time-wise.
- When capitalist entrepreneurs create a new product or service, it is usually expensive and is only available to the rich.
- Once rich customers have parted with enough money to buy the new product, the entrepreneurs have accumulated enough capital to send it to mass production, making it affordable to the middle class.
- Once the market is saturated, the government steps in, declares the product a “human right,” and provides it to the needy for free. All the costs are covered by the taxes extracted from the entrepreneurs who invented the product and from the rich who already paid for its mass production.
Therefore, THR (Time for Human Rights) = ?
I’m not a mathematician, so I will rely on the readers to help me create a sensible equation that includes timing, cost, saturation, taxation, etc. From this equation our politicians can derive time (T) when someone’s consumer product (CP) becomes everyone’s human right (HR).
Bernie Sanders recently declared categorically that healthcare is a “human right.” He didn’t mention when exactly it became a human right: at the dawn of civilization (when no one lived over thirty), during feudalism (when the village blacksmith was also the tooth surgeon), during the industrial revolution (when everything was treated with leeches), or just recently, when capital investments in R&D produced lasers and the MRI?
Is Bernie in possession of the above THR formula, which he won’t share with the toiling masses? If not, we can only conclude that he simply throws around words without knowing what they really mean, whenever he feels like it.
Without a foolproof THR formula to calculate the exact time when a consumer product becomes a “human right,” one can easily embarrass himself. Imagine if in the past the White House had expanded “human rights” to include the ownership of top hats, horse buggies, eight-track players, or VCRs. The only ones benefitting from it today would be standup comedians.
But judging by my Soviet experience, socialists are also in possession of a formula telling them when government-created “human rights” are due to expire — which always happens as soon as they gain total control of any country.
Any government powerful enough to give the people all that they want (e.g., free phones, Internet, or disposable diapers) is also powerful enough to take from the people all that they have.
And that is no laughing matter.
RELATED ARTICLE: Self-Sufficiency, Not Government Spending, Should Be the Measure of Antipoverty Progress
EDITORS NOTE: This column originally appeared in the American Thinker. The proposed equation of THR (Time for Human Rights) is now being discussed at the People’s Cube and there already are some excellent suggestions. Follow this link.








 John H. Ramsey has published “
John H. Ramsey has published “


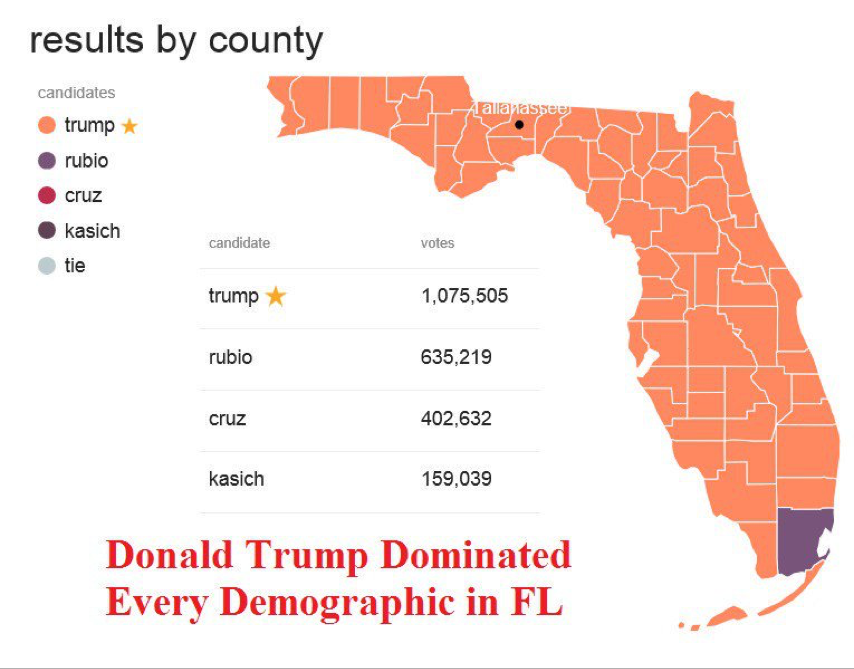 No candidate for the GOP presidential nomination has ever failed to win the sunshine state. The same holds true in the general election.
No candidate for the GOP presidential nomination has ever failed to win the sunshine state. The same holds true in the general election.
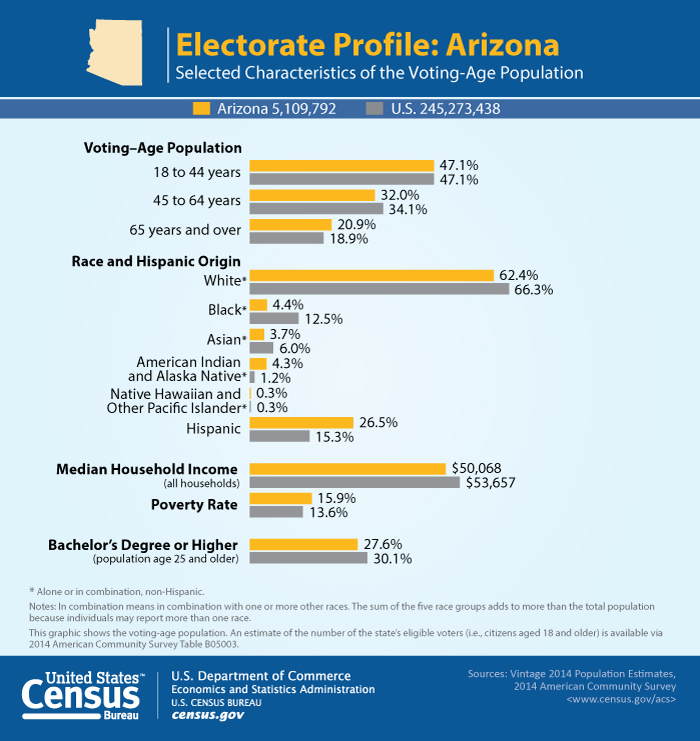
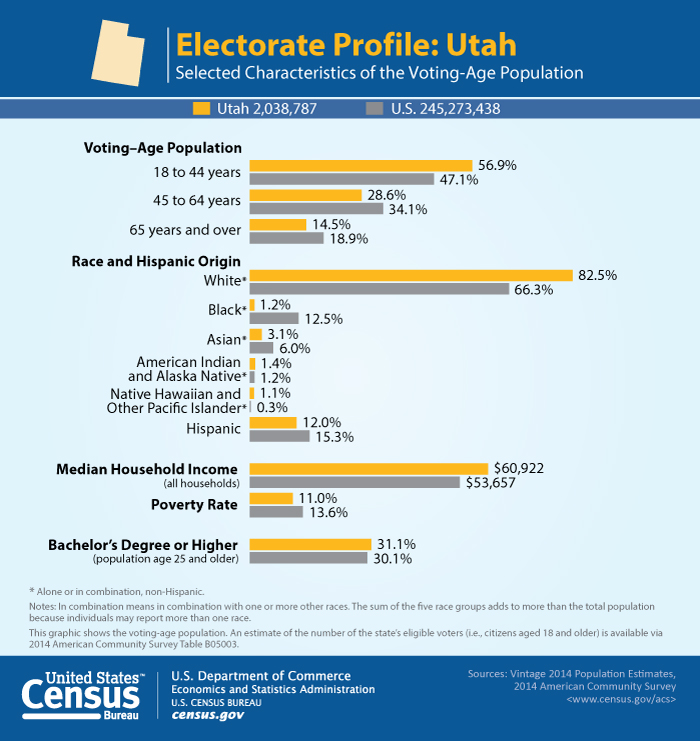




 Not only are
Not only are 



